Use Case
Use Case
SplitSecure provides digital asset custody controls for regulated financial institutions.
SplitSecure ensures that no single person, system, or vendor can move or compromise digital assets, and provides clear proof to regulators that access controls were enforced.
The financial sector is moving towards digital assets. Regulations like MiCA and frameworks like DASCP have laid the groundwork for institutions around the world to utilize these new asset classes. But with this new territory comes new access control and custody challenges.
Banks and financial institutions seeking to adopt digital assets must develop new capabilities for digital asset access and control, either in-house or working with external vendors.
Both approaches present challenges.
SplitSecure is a better alternative to either third-party vendors or fully bespoke internal asset access and control solutions.
It offers a full digital access and control solution with:
For financial institutions seeking to build in-house, Splitsecure is a platform they can leverage to ensure security and compliance.
For financial institutions seeking to work with third parties, SplitSecure sits between the bank and the vendor, controlling third-party risk and ensuring the institution remains in full control of its cryptographic material.
Even better, SplitSecure is easy to use and easy to integrate with your existing tools; no large or sophisticated cybersecurity team is required. SplitSecure has security claims suitable for the largest banks, and a setup process suitable for the smallest community bank.
SplitSecure provides comprehensive access control throughout the stack.
Depending on what your institution needs, SplitSecure can be used for:
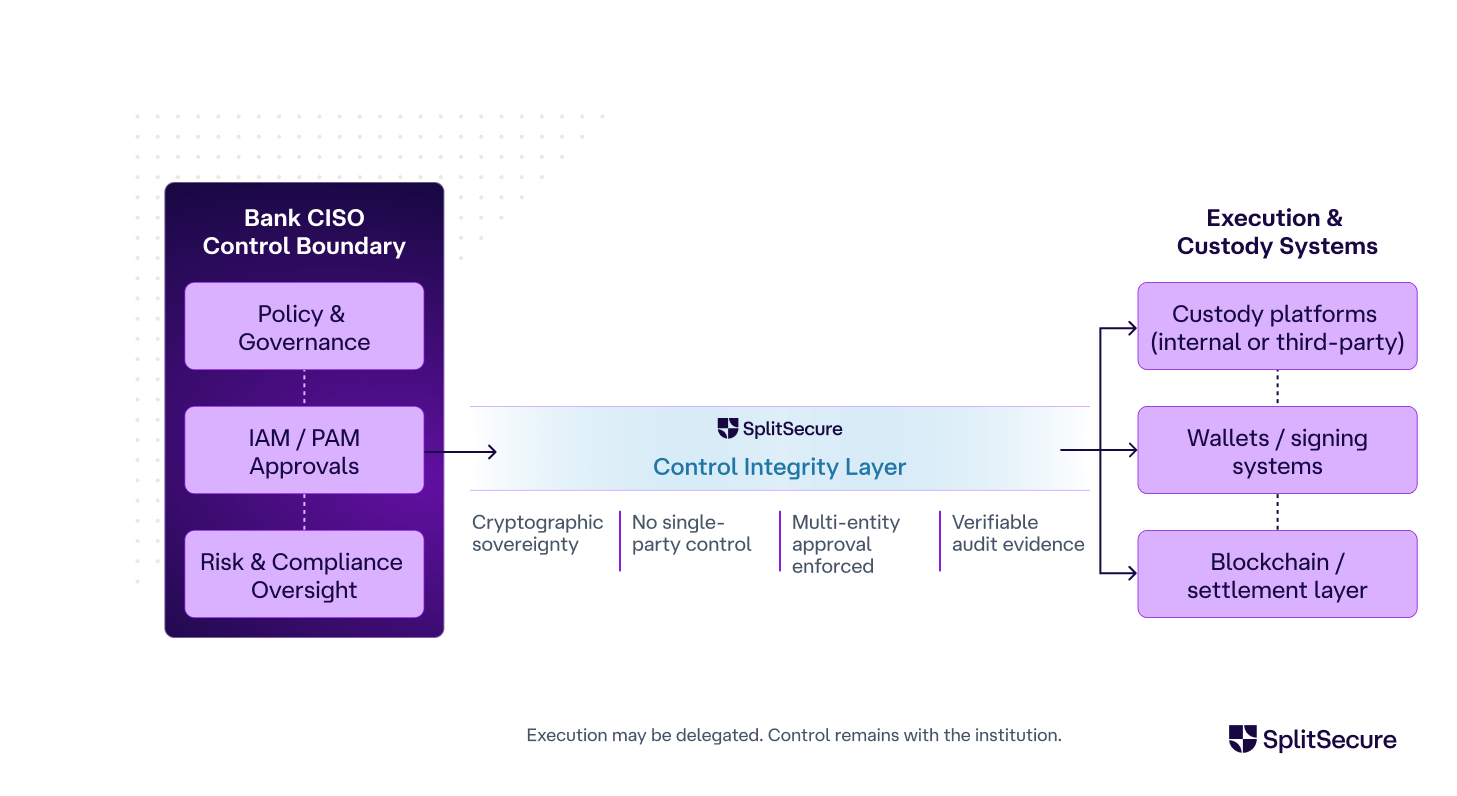
PAM/IAM (Digital asset access and control for WHO has access): SplitSecure adds a cryptographic control-integrity layer beneath the PAM/IAM approval plane, and produces externally verifiable cryptographic proofs that requirements/regulations on asset access have been followed. It provides auditor-ready evidence of segregation and multi-entity control — aligning with DASCP C10/C27 and DORA requirements.
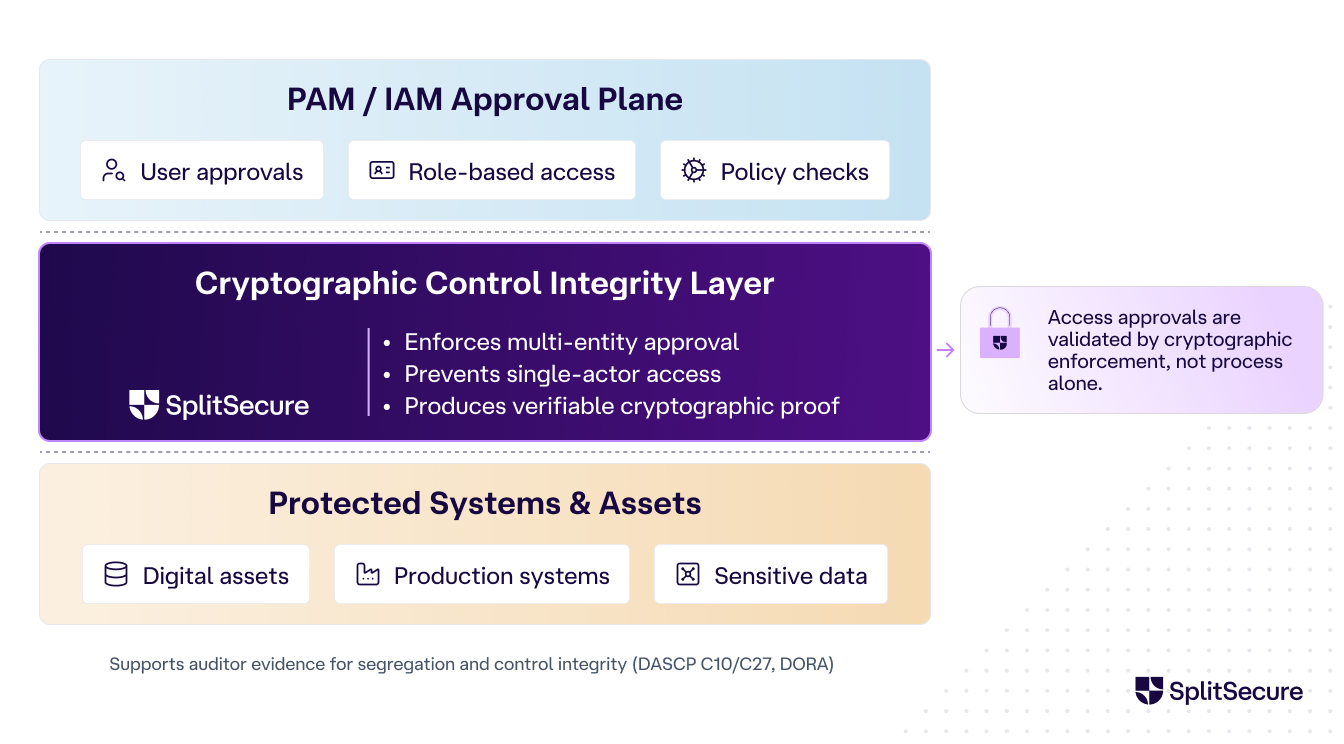
Regulatory Custodians (Solving for WHO legally holds assets): For custodians of digital assets, SplitSecure adds a cryptographic control-integrity layer above the custodian’s key-management or transaction-approval system. This enforces policy regarding the handling of those assets and provides externally verifiable proof that no single actor (not even the custodian) can unilaterally authorize the movement of client assets.
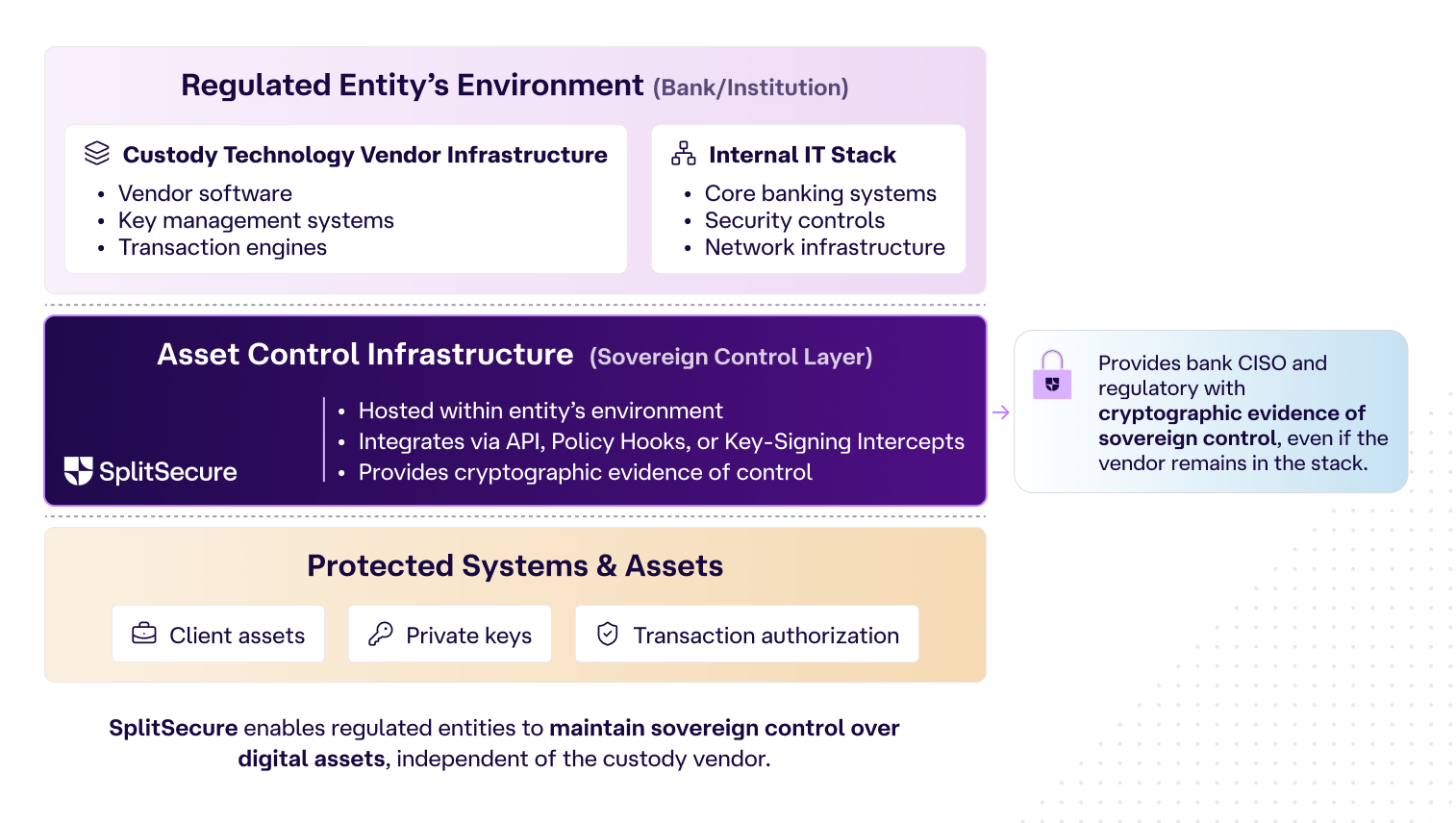
Custody Technology Vendors (Solving for WHAT is accessed): SplitSecure provides asset control infrastructure that regulated entities can host within their own environments. In this configuration, SplitSecure integrates within or above the customer’s deployed custody infrastructure (via API, policy hooks, or key-signing intercepts). This provides the bank’s CISO and regulator with cryptographic evidence of sovereign control, even if the custody software vendor remains inside the IT stack.
Compliance & Risk Management: SplitSecure makes it easy for banks to manage third-party cybersecurity risk (under NYDFS TPRM guidance). We can also help show compliance with regulations like DORA, PRA, MAS, VARA, FINMA, etc.
Inside your enterprise, you have secrets you protect with other secrets. You might have password managers protected by passwords, PAM platforms you need credentials to access, and so forth.
No matter how many layers you add, there’s always a “last secret” protecting the entire system. That last secret is a liability to your organization, and it creates risk of theft or abuse.
SplitSecure solves this problem by offering a way to protect secrets without a persistent “last secret.” It is the foundation upon which your SSO, PAM, Vault, and PKI can securely rest.
SplitSecure solves the “last secret” problem by splitting secrets & credentials across a group of devices called a team. The team can use the protected secret normally, but the secret is never persisted on any device and never leaves the environment.
You can think of this like the classic requirement to launch a nuclear missile, where two users must turn their keys at the same time. Multiple SplitSecure devices collaborate to take an action with the secret, but none of them ever possess the secret.
This architecture is powerful because it offers defense-in-depth, cryptographic sovereignty, and infinite resolution.
Because no device in the SplitSecure team ever holds the protected secret, it is not possible for an attacker to extract the secret by compromising an employee device. Even if an attacker fully compromised the devices and user accounts of your SplitSecure IT admin, they cannot grant themselves access to protected resources.
Enterprises using SplitSecure retain full control over their secrets at all times. They never have to allow a vendor to hold their secrets – even SplitSecure Inc has no access.
In SplitSecure, the team “sees” how a secret is going to be used before deciding if it should grant an access request. This means CISOs can write policies not just for when secrets may be accessed, but specifically how they may be used.
If you'd like to know more about how SplitSecure can help your organization with digital asset access and control, or if you’d like to see our technical whitepaper to get a better idea of how it works, please contact our sales team.